Inteligencia Artificial
Incluso en el mundo de la ciberseguridad, las discusiones sobre los presupuestos de seguridad empresarial tienden a desviarse hacia lo mundano. Sin embargo, el macroentorno actual ha frustrado casi todas las predicciones del mercado, y aunque sabemos con certeza que el mercado a la baja ha llevado a la mayoría de las empresas a la austeridad, su verdadero impacto en el gasto en seguridad cibernética sigue siendo un enigma, hasta el día de hoy.
Un informe de YL Ventures basado en datos extraídos de encuestas a los CISO (directores de seguridad de la información) de Fortune 1000 y a los responsables de la toma de decisiones de seguridad cibernética, arroja algo de luz sobre el impacto del mercado a la baja en el comportamiento de compra, cómo las estrategias de seguridad están evolucionando en respuesta y cómo las interacciones de los clientes con los proveedores han cambiado a medida como resultado de todo ello.
La mitad de los CISO aún tienen margen para adaptarse a nuevas soluciones y, contrariamente a las bajas expectativas, el 45 % de los presupuestos de seguridad cibernética se mantuvieron sin cambios o incluso se incrementaron. Específicamente, un tercio de los encuestados (33,3 %) reporta presupuestos sin cambios y el 12,2 % vio aumentar sus presupuestos.
Mientras tanto, otro tercio (33,3 %) de los presupuestos de seguridad cibernética se han recortado, mientras que el 21,2 % de los líderes de seguridad cibernética actualmente manejan presupuestos congelados, lo que significa que no es posible realizar nuevo gasto.
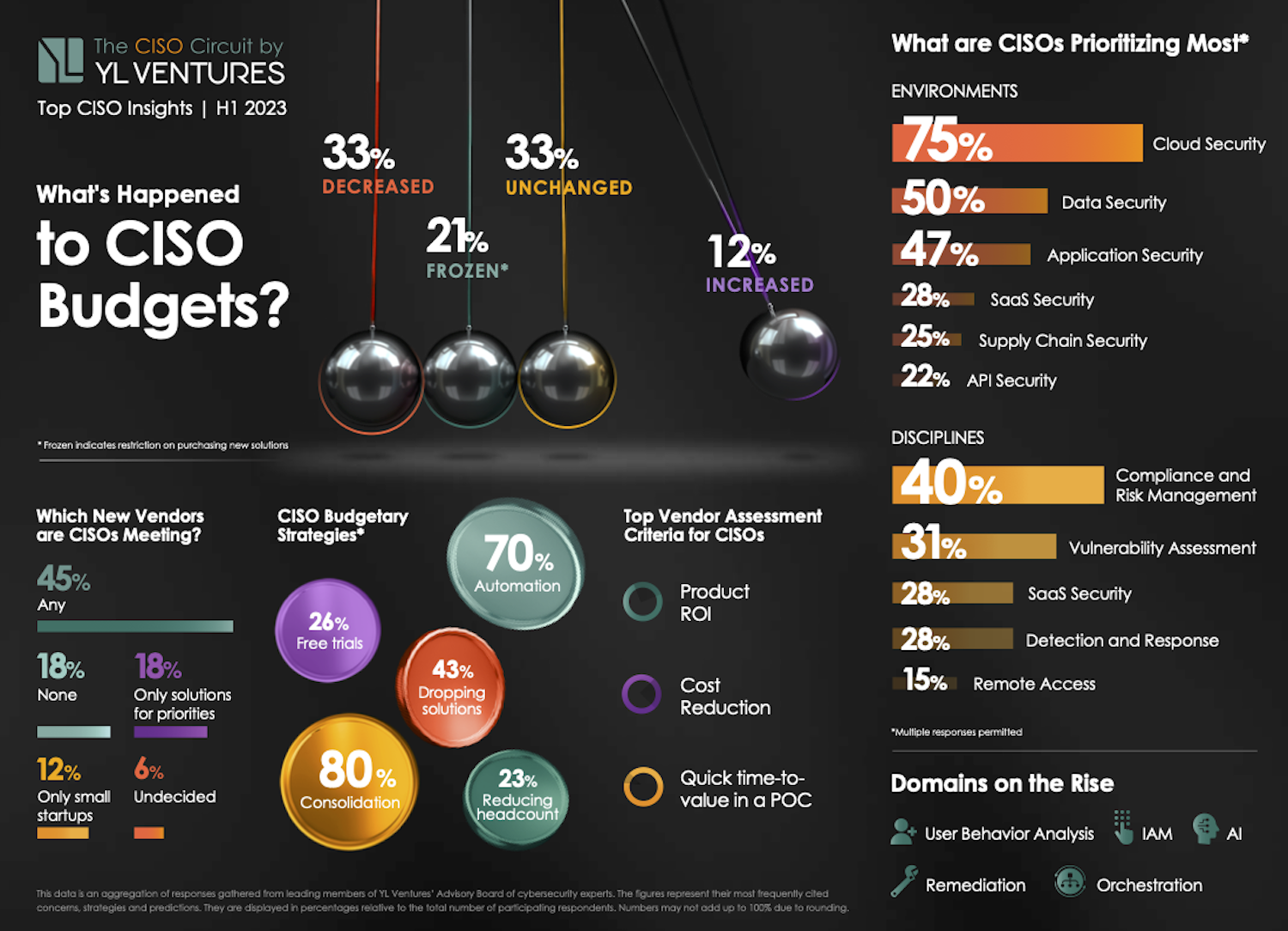
Imagen: Infome YL
Hacer el primer contacto
Aunque los datos pueden parecer intimidantes, los proveedores aún tienen muchas oportunidades. Una mayoría considerable (75,8 %) de los líderes en seguridad cibernética todavía están dispuestos a conocer nuevos proveedores; simplemente hay más factores que tienen en consideración para la toma de decisiones. Si bien casi la mitad (45,5 %) está dispuesta a conocer a cualquier proveedor, el 18,2 % solo se reúne con aquellos que abordan estrictamente sus prioridades de seguridad más apremiantes y el 12,1 % solo está interesado en conocer nuevas empresas más jóvenes y pequeñas.
De hecho, este es un excelente momento para que las pequeñas empresas emergentes brillen y quizás para que los proveedores más grandes tomen nota. A los ojos de la mayoría de los líderes de seguridad cibernética, las empresas más pequeñas y en etapas iniciales tienden a ofrecer costes de licencia más ventajosos, así como asociaciones de diseño, que permiten soluciones a medida que se adaptan mejor a sus puntos débiles y necesidades operativas únicas.
Actualmente, el 26,7% de los encuestados confían en los servicios gratuitos como medio provisional. Si recordamos los días más difíciles de la pandemia, cuando muchos proveedores de seguridad cibernética ofrecían sus servicios de forma gratuita, podemos ver una amplia evidencia de cuánta buena voluntad crearon esos gestos y cómo impulsaron a muchas empresas a la cima. Para los vendedores que encuentran esto demasiado difícil de digerir, considere qué tan efectivas han sido las tácticas de tierra y expansión en el pasado, y recuerde que la creciente ola de conservadurismo fiscal deja poco espacio para la obstinación en solicitud de mayores gastos.
La necesidad de contratos flexibles queda más clara a partir de las solicitudes explícitas de los propios CISO. Muchos CISO que participaron en el informe tuvieron palabras duras para los proveedores que se acercan a ellos con grandes contratos tras despidos o cierres masivos. Tienen peores juicios para quienes todavía confían en la táctica obsoleta de sembrar miedo, incertidumbre y duda en torno al panorama de amenazas. En tiempos tan difíciles sin un final a la vista, difundir más negatividad no es la manera de ganarse los corazones.
La regla de oro de comprender las necesidades de los clientes ha adquirido dimensiones adicionales, a medida que cada empresa experimenta su propio recorrido de presión financiera. Los proveedores que puedan ser sensibles a ello llegarán mucho más lejos que aquellos que no lo sean.
Hablando el mismo idioma
El espíritu de austeridad, incluso entre los CISO cuyos presupuestos han aumentado, está volviendo a priorizar la forma en que se evalúan las adquisiciones de nuevos productos. Los verdaderos veteranos de la ciberseguridad ya están familiarizados con el proceso de luchar por la aprobación de nuevas compras, generalmente con la ayuda de un ROI (retorno de la inversión) demostrable. Esta experiencia vuelve a resultar útil, ya que el retorno de la inversión (ROI) y la reducción de costes se convierten en factores más importantes que nunca en la toma de decisiones.
Juntos, el retorno de la inversión (ROI) y la reducción de costos constituyen el 60% de los principales criterios de proveedores que buscan los CISO, convirtiéndose en su principal factor decisivo en la adquisición de productos. Los proveedores que no puedan demostrar los retornos que los CISO tendrán dificultades para sobrevivir en el panorama frugal actual.
El informe también revela exactamente cómo esta frugalidad se manifiesta en la estrategia real de ciberseguridad empresarial. Durante mucho tiempo, los líderes de ciberseguridad han estado decididos a racionalizar sus operaciones (lo que ahora implica la orquestación de muchos departamentos) y desinflamar sus pilas de seguridad. Ahora están bajo más presión que antes para hacerlo. Según los líderes de ciberseguridad encuestados, el 80% está centrando sus esfuerzos en consolidar sus soluciones, el 43,3% ha rescindido al menos un contrato con un proveedor, el 70% depende más de la automatización y el 23,3% ha tenido que despedir personal.
Hay mucho que interpretar de estos datos. Lo primero puede no ser sorprendente y, sin embargo, los CISO se encuentran repitiendo lo mismo a diario: los proveedores deben dejar de vender funciones como plataformas. Así es como sus stacks crecieron tanto en el inicio. A las soluciones puntuales tampoco les irá mucho mejor en estos días, ya que la mayoría de los equipos de seguridad tienen demasiado escasez de personal para dedicar tiempo a aprender nuevas tecnologías o clasificar más alertas. Sin embargo, aquellos que pueden demostrar una pequeña curva de aprendizaje y una fácil integración aún pueden tener una oportunidad si resuelven un problema prioritario para los CISO.
La consolidación es verdaderamente el nombre del juego para los emprendedores que buscan construir grandes empresas. Los discursos que demuestran cómo una única solución puede dar sentido al ruido o incluso reemplazar varias otras tienen muchas más probabilidades de ganarse a los CISO. También recuerda otra tendencia importante: las medidas de austeridad están fomentando el regreso a lo básico.
Centrándonos en lo que importa
La principal prioridad actual es proteger los entornos empresariales existentes con la máxima eficiencia y cubrir los puntos ciegos aún existentes. A pesar de los equipos y soluciones sobredimensionadas e incluso superpuestas, muchas áreas importantes de protección siguen desatendidas. Cuando a los encuestados se les dio la opción de seleccionar múltiples áreas de enfoque, las siguientes áreas recibieron la mayor atención: en lo que respecta a los entornos, el 75 % prioriza la seguridad en la nube, el 50 % la seguridad de los datos, el 46,9 % la seguridad de las aplicaciones, el 25 % la seguridad de la cadena de suministro, 28,1% seguridad SaaS y 21,9% seguridad API.
El impulso hacia la seguridad general y básica se refleja también en las disciplinas que están priorizando: el 40,6% prioriza el cumplimiento y la gestión de riesgos, el 31,3% la evaluación de vulnerabilidades, el 28,1% la detección y respuesta y el 15,6% el acceso remoto. Esta lista puede parecer sorprendente al principio. ¿Dónde está IAM? ¿Qué tal la orquestación, la remediación y el análisis del comportamiento del usuario? Lo más notoriamente ausente, por supuesto, es la IA. Esto no quiere decir que los CISO no estén expresando interés en estas áreas, sino todo lo contrario.
Al menos en lo que respecta a la IA, muchos CISO están esperando el momento oportuno para encontrar una solución adecuada y utilizando las herramientas existentes para ayudarles a ver y gestionar el riesgo generativo de la IA lo mejor que pueden mientras tanto. O simplemente están prohibiendo por completo el uso de IA generativa. En cuanto al otro tipo de soluciones, todavía no hay datos concretos disponibles para evaluar de forma cuantificable el interés. No obstante, vemos un marcado aumento en este tipo de soluciones en el mercado y podemos esperar que el interés en ellas crezca durante el próximo año.
Incluso en lo que parece un desierto de clientes, los proveedores que juegan bien sus cartas aún pueden salir airosos. Esto es especialmente cierto para aquellos que pueden aportar esta valiosa experiencia para guiar las estrategias de los CISO en estas áreas en lugar de proporcionar meras advertencias sobre los riesgos involucrados.